Enterprise-grade security. Built by design. Enforced by default.
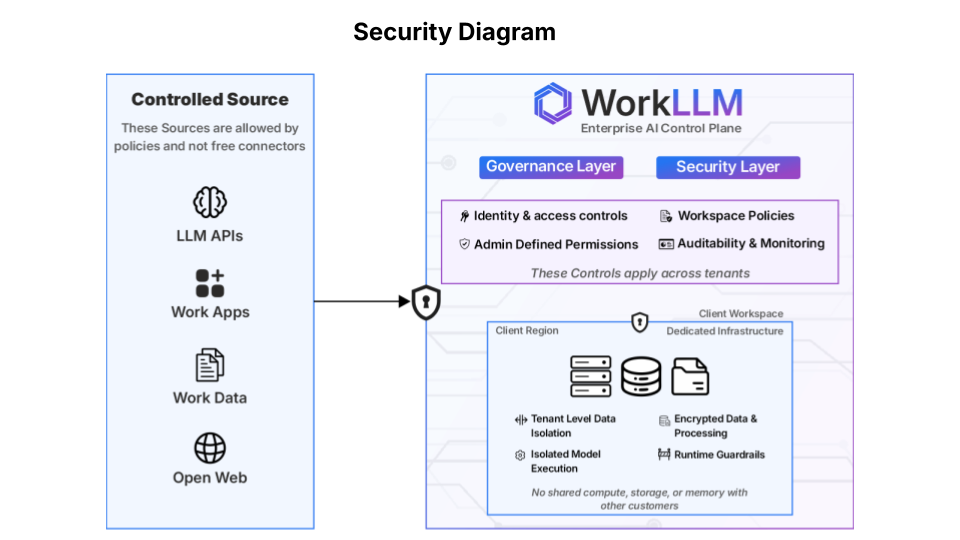
WorkLLM is built to meet the security, privacy, and compliance expectations of modern enterprises with a dedicated cloud tenant for every customer. From day one, your data is isolated, encrypted, auditable, and governed by strict enterprise-level access controls.
Trusted by enterprises





Our Security Philosophy
Security at WorkLLM is built on four foundational principles that guide every architectural and product decision we make.
Built for Enterprise Trust
Least Privilege Access
Accountability, Not Assumption
Enterprise Transparency
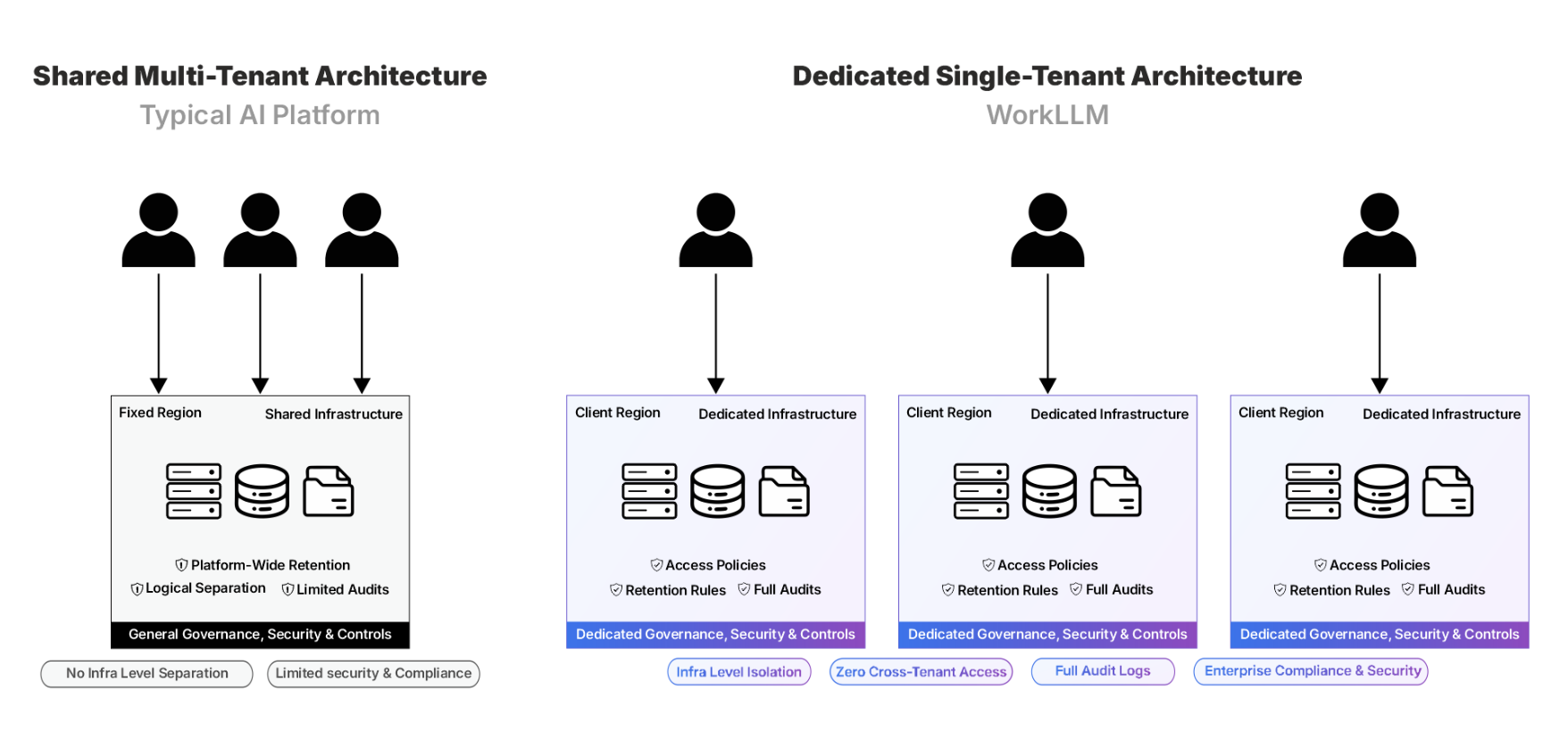
Dedicated Tenant Architecture
What This Enables?
- No Cross-Tenant Exposure — Customer data never mixes with other tenants, by design.
- Independent Auditability — Each workspace maintains its own activity logs and governance trail.
- Enterprise Readiness — Simplifies security reviews and supports regulated and high-compliance environments.
What's Isolated?
- Customer Data — Conversations, documents, and metadata are isolated within each customer’s tenant.
- AI Context & Embeddings — Vector stores and retrieval are scoped per tenant to prevent cross-workspace context leakage.
- Access & Permissions — Authentication rules and role-based access controls are enforced independently per workspace.
Security Capabilities
Encryption At Rest & Transit
All customer data is encrypted at rest and protected in transit using modern industry standards to prevent unauthorized access.
Role-Based Access Control (RBAC)
Granular permissions ensure users and services only access what they’re authorized to — nothing more.
SSO & Authentication
Secure authentication with optional SAML-based SSO support for enterprise deployments.
Audit Logs & Activity Tracking
All meaningful actions are logged within each workspace to support compliance, investigations, and internal reviews.
Input & Output Guardrails
Automatically redact sensitive data, enforce prompt restrictions, and maintain safe output policies across the workspace.
No Training On Customer Data
Customer data is never used to train models and is processed transiently for inference only.
Zero Data Retention At the LLM Layer
Requests to the LLM providers are not retained by them, providing zero data retention at the LLM layer.
Admin Control & Visibility
Workspace admins control integrations, sharing, usage visibility, and access revocation from a central dashboard.
FAQs
Is our data isolated from other customers?
Yes. Every WorkLLM customer is provisioned into a dedicated cloud tenant. Data, AI context, embeddings, and access controls are isolated per tenant to prevent any cross-customer exposure.
Does WorkLLM use our data to train AI models?
No. Customer data is never used to train models. Prompts are processed only for inference and are not retained for training purposes.
What does “zero data retention at the LLM layer” mean?
Requests to the LLM providers are processed transiently at the model layer and are not retained, providing zero data retention at the LLM layer.
Where is our data stored?
Customer data is stored securely within your dedicated tenant, isolated from other organizations and accessible only to your workspace.
What access controls are available?
WorkLLM supports role-based access control (RBAC), allowing administrators to define permissions across users, assistants, agents, and integrations.
Are users actions auditable?
Yes. All meaningful actions — including access changes, configuration updates, and data usage — are logged and available to workspace administrators.
How is data encrypted?
All customer data is encrypted at rest and protected in transit using modern, industry-standard encryption protocols.
How does WorkLLM prevent unauthorized access?
Access is controlled through authentication, role-based permissions, session management, and tenant-level isolation across infrastructure and application layers.
Is WorkLLM suitable for regulated or high-compliance environments?
Yes. WorkLLM is designed with strong isolation, auditability, and access controls that support regulated and high-compliance use cases.
How can our security team get more information?
Security and compliance questions can be directed to info@workllm.io, and we’re happy to support security reviews or questionnaires.
Happy Customers
Customer satisfaction is our major goal. See what our customers are saying about us.
“Vivamus sagittis lacus vel augue laoreet rutrum faucibus dolor auctor. Vestibulum id ligula porta felis euismod semper. Cras justo odio dapibus facilisis sociis natoque penatibus.”

Coriss Ambady
Financial Analyst ABC.com
“Vivamus sagittis lacus vel augue laoreet rutrum faucibus dolor auctor. Vestibulum id ligula porta felis euismod semper. Cras justo odio dapibus facilisis sociis natoque penatibus.”

Cory Zamora
Marketing Specialist ABC.com
“Vivamus sagittis lacus vel augue laoreet rutrum faucibus dolor auctor. Vestibulum id ligula porta felis euismod semper. Cras justo odio dapibus facilisis sociis natoque penatibus.”

Nikolas Brooten
Sales Specialist Financial Analyst ABC.com
“Vivamus sagittis lacus vel augue laoreet rutrum faucibus dolor auctor. Vestibulum id ligula porta felis euismod semper. Cras justo odio dapibus facilisis sociis natoque penatibus.”

Coriss Ambady
Financial Analyst Financial Analyst ABC.com
“Vivamus sagittis lacus vel augue laoreet rutrum faucibus dolor auctor. Vestibulum id ligula porta felis euismod semper. Cras justo odio dapibus facilisis sociis natoque penatibus.”

Jackie Sanders
Investment Planner Financial Analyst ABC.com
“Vivamus sagittis lacus vel augue laoreet rutrum faucibus dolor auctor. Vestibulum id ligula porta felis euismod semper. Cras justo odio dapibus facilisis sociis natoque penatibus.”

Laura Widerski
Sales Specialist Financial Analyst ABC.com